
Security-savvy organizations understand that it's best to assume that their systems are breached. It's one reason why zero-trust architectures get so ...
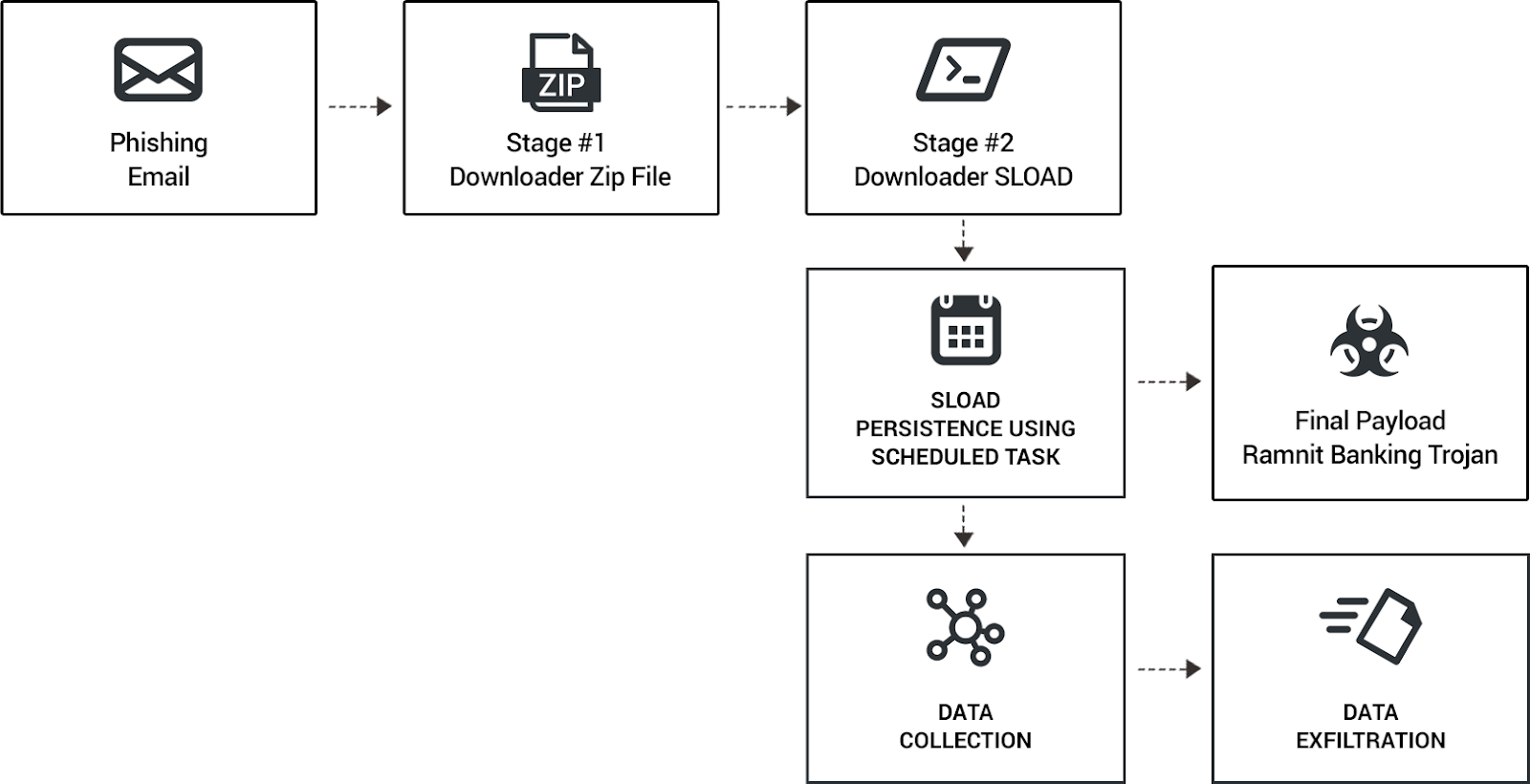
Research by Eli Salem, Lior Rochberger, & Niv Yona Introduction Cybereason’s Nocturnus and Active Hunting Service are two teams dedicated to easil...

Attackers are actively exploiting an unpatched remote code execution (RCE) vulnerability in a Windows component called the Microsoft Support Diagnosti...
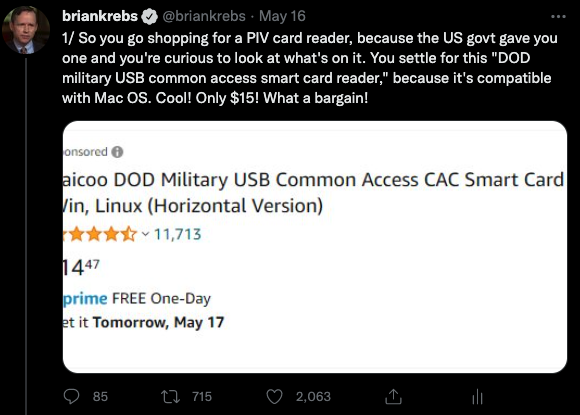
Millions of U.S. government employees and contractors have been issued a secure smart ID card that enables physical access to buildings and controlled...

The CSO Hall of Fame was created to spotlight outstanding leaders who have significantly contributed to the practice of information risk management an...

The CSO50 awards recognize security projects that demonstrate outstanding thought leadership and business value. The awards are scored according to a...