
What is a logic bomb? A logic bomb is a piece of code left lying in wait on a computer that will execute under certain specified conditions and take ...

Software-defined wide area networking, or SD-WAN, is the next frontier for the network edge. Multiple analysts report that the SD-WAN market is in the...

Xerxes Kiok Kan – Head of IT Security & Controls at Anglo-Eastern – joins Xiou Ann Lim for this CSO Executive Sessions interview. They discuss nur...

What is SAML and what is it used for? The Security Assertion Markup Language (SAML) is an open standard that allows security credentials to be shared...

If you have a traditional domain, it’s time to audit your Active Directory. In fact, it’s probably way past time. You probably have accounts that ...
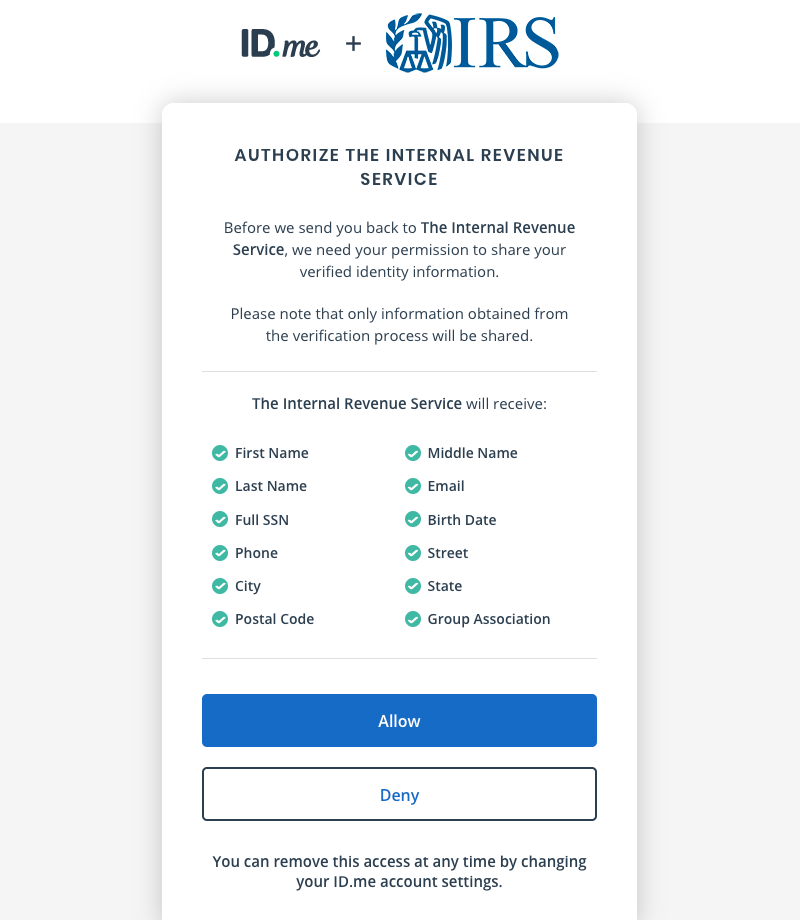
If you created an online account to manage your tax records with the U.S. Internal Revenue Service (IRS), those login credentials will cease to work l...